Network Attacks Through a Step-by-Step Attack Simulation
Jeff Wolverton
Overview of a Network Attacks Simulation
Dive into a practical demonstration of a network attack, tracing its progression across six pivotal stages—from Initial Access to Data Exfiltration. Learn how attackers leverage basic tools to stay hidden and discover why having multiple layers of defense is critical.
Most network threats surprisingly don’t rely on high-tech or obscure zero-day exploits. Instead, they exploit well-known vulnerabilities using readily available tools. Through this simulation based on real-world models like the c, Atomic Red Team, and insights from Cato Networks and public threat intelligence, security teams can test their defenses, ensure robust multi-layer security, and showcase the significance of network security to their leadership.
The Benefits of Simulating Network Attacks
Simulating an attack provides critical insights:
- It tests detection systems to intercept common and subtle threats.
- It highlights the necessity of having several defensive layers, as single-point defenses often fail.
- It underscores the importance of network monitoring, giving leadership a clear view of potential breaches and effective countermeasures.
Detailed Attack Simulation
- Initial Access: The simulation begins with a spear-phishing attempt—perhaps an enticing job offer emailed to an employee. This email contains a macro-laden attachment that exploits a vulnerability in Microsoft Office to run a reverse shell called Hoaxshell.
Dolev Attiya, a security engineer, notes, “A layered defense strategy is essential from the start. The phishing attempt and the exploit could be detected through multiple controls like email scanning, endpoint antivirus, or network monitoring.”
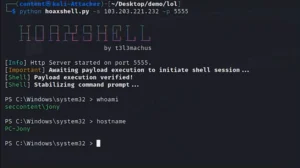
2. Ingress Tool Transfer: Post-access, the attacker introduces tools like Powershell and Mimikatz into the system, tools that are commonly part of the Windows environment but are repurposed here for malicious activities.
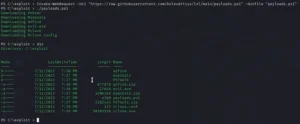
3. Discovery: The attacker maps the network, identifying critical assets such as servers, workstations, and domain controllers, much like a tourist navigating a new city.
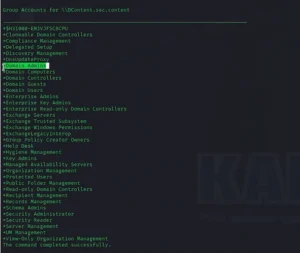
4. Credential Dumping: Using the tools deployed earlier, the attacker extracts credentials from various systems, preparing for the next phase.
5. Lateral Movement and Persistence: With these credentials, the attacker spreads laterally across the network, aiming to reach as many systems and gain as high privileges as possible. This phase is crucial for setting up long-term access and preparing for eventual data extraction.
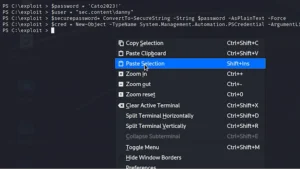
Etay Maor, a security strategist, comments, “The ubiquity of tools like Mimikatz in such attacks underlines their effectiveness in bypassing security measures within seconds.”
6. Data Exfiltration: The final stage involves identifying and siphoning off valuable data, which might be uploaded to a cloud service or encrypted for a ransomware attack.
Strategies for Enhanced Network Protection
To guard against such attacks, a multi-layered security approach is vital. Effective protection involves strategic and holistic management of all security layers within the attack chain, preparing for every possible move by an attacker to fortify the network’s defenses. Reach out to us at PivIT Strategy to start a conversation of protecting yourself further.
Jeff Wolverton
Jeff, the CEO of PivIT Strategy, brings over 30 years of IT and cybersecurity experience to the company. He began his career as a programmer and worked his way up to the role of CIO at a Fortune 500 company before founding PivIT Strategy.
